Profiling a Rogue Fast-Flux Botnet Infrastructure That’s Currently Hosting Multiple Online Cybercrime Enterprises - An Analysis

Sample screenshot of an E-shop for stolen credit cards information hosted on the botnet’s rogue and malicious C&C fast-flux infrastructure
We’ve recently decided to map and research various domain registrations made by well-known and established online cybercriminals. We took several hundred emails known to belong to well-known cybercriminals and decided to cross-check them for related domain registrations by using Maltego and WhoisXML API’s vast and in-depth real-time and historical WHOIS records database.
In this article, we’ll thoroughly discuss the relevant findings for this study based on several hundred email addresses known to be owned and operated by known cybercriminals and checked them for related domain registrations. Then we will provide actionable intelligence on the online infrastructure of these newly discovered domains known to be managed and registered by known cybercriminals.
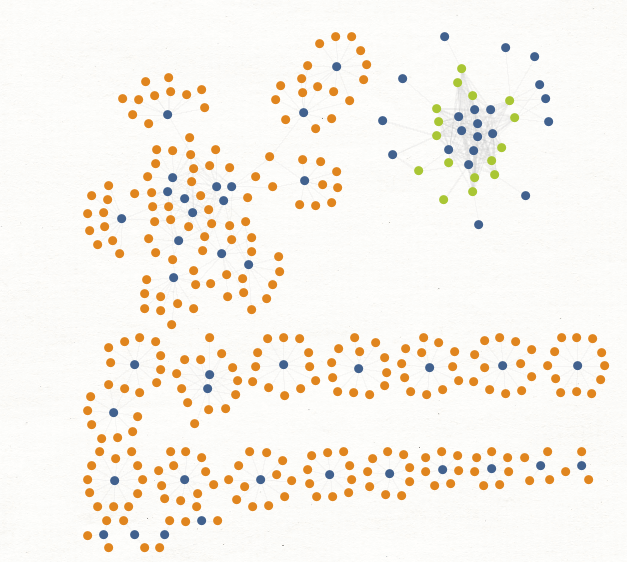
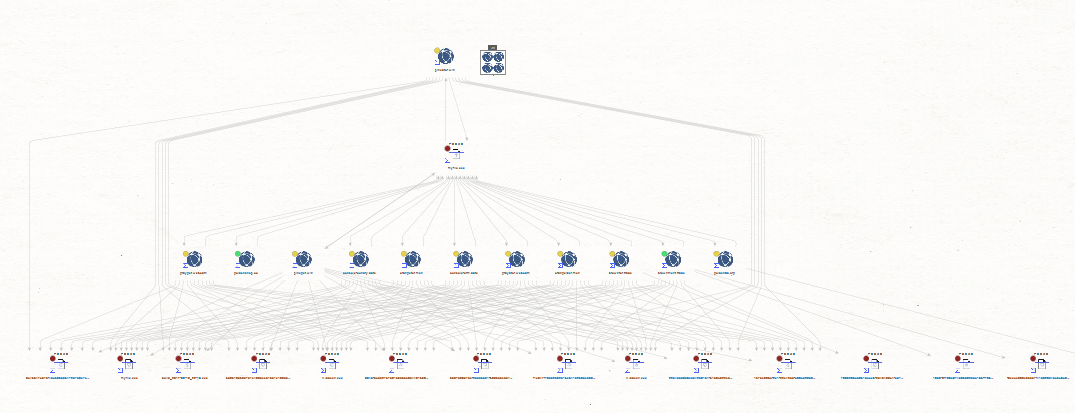
Sample Maltego Graph of the Rogue E-Shops for stolen credit cards information portfolio of domains including their associated responding IPs
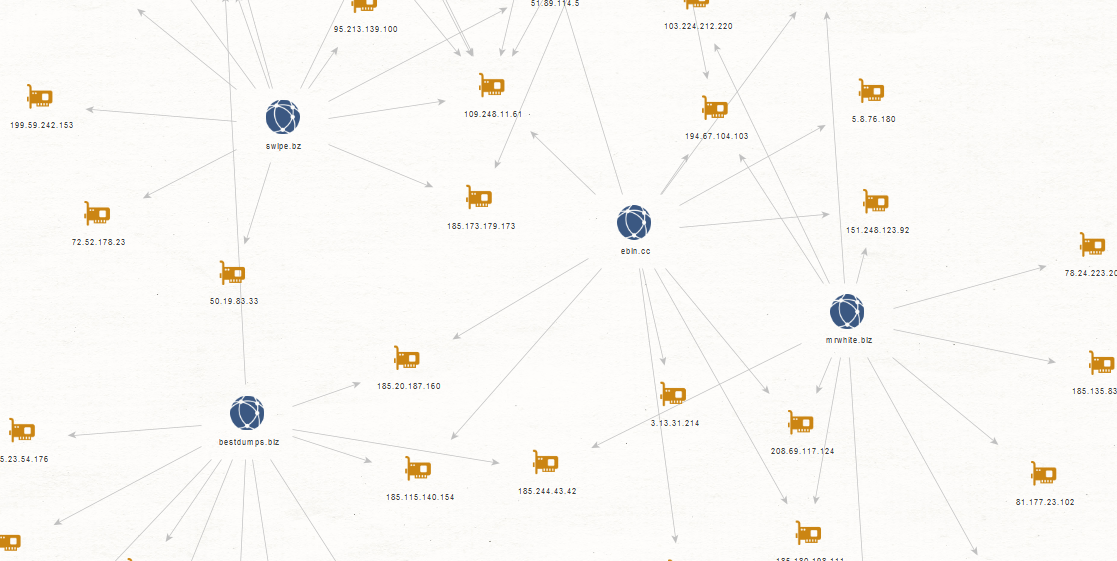
We decided to sample some malicious activity from the botnet’s fast-flux infrastructure, look for E-Shops selling access to stolen credit card information and provide actionable intelligence on the infrastructure behind these E-Shops. In particular, we focus on their responding IPs, looking for additional clues regarding malicious MD5s that are actually phoning back to and using the same infrastructure using VirusTotal’s API.
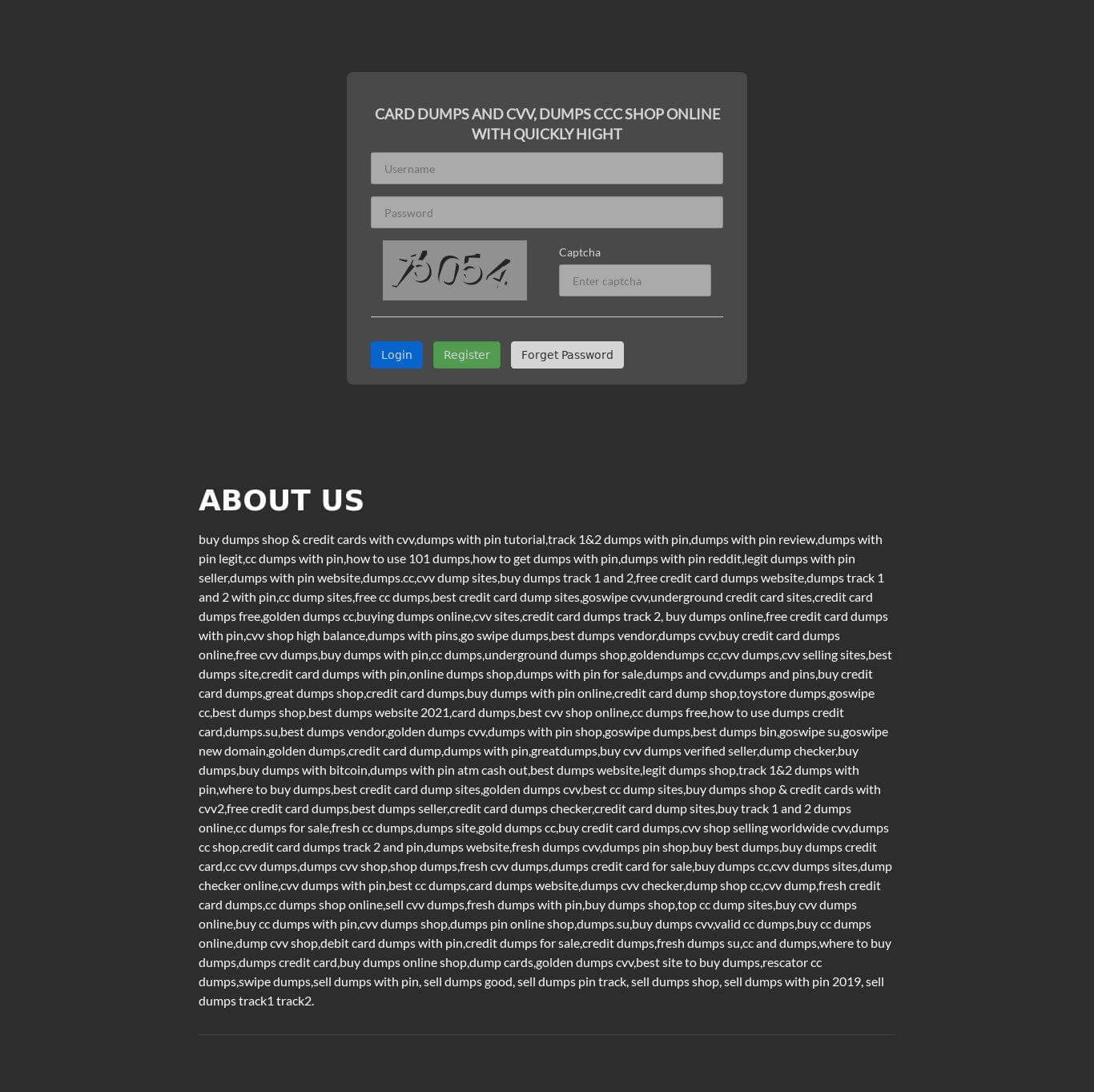
Sample Web Site Hosted on the Botnet’s rogue fast-flux C&C Infrastructure, which in reality is an E-Shop for selling stolen credit cards information

Sample Web Site Hosted on the Botnet’s rogue fast-flux C&C Infrastructure, which in reality is an E-Shop for selling stolen credit cards information

Sample Web Site Screenshot of the infamous hxxp://omerta.cc cybercrime-friendly forum community that’s also sharing the same hosting infrastructure
Sample Maltego Graph of the Rogue E-Shops for stolen credit cards information portfolio of domains including their associated responding IPs
Sample Web Site Hosted on the Botnet’s rogue fast-flux C&C Infrastructure, which in reality is an E-Shop for selling stolen credit cards information
Sample Web Site Hosted on the Botnet’s rogue fast-flux C&C Infrastructure, which in reality is an E-Shop for selling stolen credit cards information
Sample Web Site Hosted on the Botnet’s rogue fast-flux C&C Infrastructure, which in reality is an E-Shop for selling stolen credit cards information
Sample Web Site Hosted on the Botnet’s rogue fast-flux C&C Infrastructure, which in reality is an E-Shop for selling stolen credit cards information
Sample portfolio of rogue and currently active online E-Shops for selling stolen credit cards information hosted on the botnet’s fast-flux C&C infrastructure:
- bestdump[.]org
- bestdumps[.]biz
- briansclub[.]at
- briansclub[.]cm
- brocard1[.]net
- buybestbiz[.]net
- c2bit[.]pw
- carderbay[.]com
- cardhouse[.]cc
- ddumps24[.]com
- deluxedumps[.]com
- diamondumps[.]biz
- ebin[.]cc
- entershop[.]st
- fe-shop[.]link
- flyded[.]gs
- freshstuff24[.]net
- fullzshop[.]su
- fullzstore[.]su
- goldenshop[.]cc
- goodshopbiz[.]net
- greendumps24[.]biz
- kingven[.]cc
- luckytrack[.]cc
- mrwhite[.]biz
- pabloescobar[.]biz
- russianmarket[.]gs
- russianmarket[.]zone
- shadowcarders[.]com
- smd1[.]la
- stardumps24[.]com
- tiesto[.]ec
- topcc[.]store
- vendta[.]cc
- worldcvv[.]me
- wt1[.]la
- wt1shop[.]org
- www[.]fe-acc18[.]ru
- yohohobay[.]cc
- Swipe[.]bz
Responding IPs of the fraudulent E-Shops for stolen credit card information as part of a botnet’s fast flux hosting infrastructure:
- 35[.]199[.]65[.]220
- 129[.]226[.]192[.]109
- 35[.]188[.]45[.]236
- 78[.]41[.]204[.]33
- 78[.]41[.]204[.]29
- 78[.]41[.]204[.]38
- 78[.]41[.]204[.]35
- 78[.]41[.]204[.]34
- 78[.]41[.]204[.]28
- 78[.]41[.]204[.]31
- 78[.]41[.]204[.]30
- 35[.]234[.]120[.]206
- 35[.]242[.]170[.]33
- 35[.]205[.]152[.]183
- 35[.]246[.]16[.]37
- 35[.]246[.]78[.]112
- 35[.]241[.]199[.]75
- 35[.]228[.]99[.]65
- 8[.]209[.]73[.]178
- 35[.]198[.]175[.]43
- 195[.]19[.]192[.]26
- 104[.]27[.]152[.]51
- 109[.]248[.]11[.]229
- 190[.]115[.]18[.]200
- 172[.]67[.]211[.]232
- 104[.]27[.]153[.]51
- 46[.]173[.]219[.]103
- 104[.]27[.]165[.]81
- 156[.]234[.]71[.]98
- 104[.]27[.]164[.]81
- 104[.]21[.]85[.]119
- 172[.]67[.]205[.]151
- 78[.]41[.]204[.]37
- 5[.]79[.]68[.]103
- 78[.]41[.]204[.]26
- 209[.]126[.]123[.]12
- 81[.]90[.]180[.]59
- 185[.]22[.]152[.]157
- 104[.]24[.]105[.]8
- 31[.]220[.]2[.]84
- 8[.]208[.]77[.]140
- 104[.]24[.]104[.]8
- 198[.]144[.]121[.]105
- 169[.]47[.]130[.]88
- 104[.]27[.]157[.]214
- 169[.]47[.]130[.]87
- 104[.]27[.]156[.]214
- 104[.]18[.]47[.]175
- 169[.]47[.]130[.]86
- 104[.]27[.]144[.]53
- 169[.]47[.]130[.]85
- 104[.]27[.]145[.]53
- 104[.]18[.]46[.]175
- 169[.]47[.]130[.]83
- 104[.]27[.]134[.]138
- 172[.]67[.]180[.]56
- 169[.]47[.]130[.]84
- 172[.]67[.]211[.]134
- 104[.]21[.]51[.]63
- 169[.]47[.]130[.]81
- 172[.]64[.]165[.]26
- 172[.]67[.]222[.]226
- 169[.]47[.]130[.]82
- 104[.]27[.]135[.]138
- 169[.]47[.]130[.]79
- 104[.]21[.]60[.]33
- 169[.]47[.]130[.]80
- 172[.]64[.]164[.]26
- 172[.]67[.]191[.]31
- 185[.]207[.]204[.]211
- 185[.]145[.]128[.]177
- 104[.]18[.]37[.]167
- 77[.]72[.]0[.]126
- 185[.]254[.]188[.]237
- 104[.]18[.]36[.]167
- 45[.]33[.]20[.]235
- 124[.]156[.]183[.]249
- 72[.]14[.]185[.]43
- 119[.]28[.]57[.]199
- 104[.]243[.]45[.]179
- 45[.]33[.]30[.]197
- 124[.]156[.]188[.]168
- 103[.]224[.]212[.]222
- 93[.]187[.]129[.]248
- 72[.]14[.]178[.]174
- 119[.]28[.]30[.]152
- 119[.]28[.]49[.]50
- 185[.]143[.]223[.]153
- 103[.]239[.]29[.]151
- 194[.]67[.]71[.]148
- 173[.]255[.]194[.]134
- 185[.]178[.]208[.]185
- 104[.]23[.]128[.]56
- 185[.]173[.]179[.]173
- 104[.]23[.]129[.]56
- 103[.]9[.]77[.]212
- 109[.]248[.]11[.]61
- 89[.]111[.]167[.]3
- 95[.]213[.]139[.]100
- 49[.]51[.]132[.]214
- 93[.]170[.]130[.]136
- 104[.]27[.]167[.]155
- 210[.]56[.]60[.]227
- 51[.]89[.]114[.]5
- 104[.]27[.]166[.]155
- 185[.]38[.]142[.]78
- 45[.]33[.]18[.]44
- 194[.]67[.]71[.]21
- 104[.]27[.]140[.]117
- 172[.]67[.]146[.]17
- 104[.]27[.]141[.]117
- 104[.]21[.]63[.]139
- 91[.]92[.]70[.]18
- 95[.]213[.]139[.]109
- 95[.]181[.]178[.]236
- 36[.]110[.]114[.]130
- 185[.]132[.]53[.]221
- 91[.]210[.]168[.]204
- 198[.]105[.]254[.]11
- 185[.]132[.]53[.]231
- 109[.]70[.]26[.]37
- 82[.]151[.]108[.]118
- 194[.]85[.]61[.]76
- 185[.]132[.]53[.]219
- 111[.]90[.]149[.]200
- 72[.]52[.]178[.]23
- 104[.]18[.]43[.]18
- 111[.]90[.]138[.]208
- 50[.]19[.]83[.]33
- 172[.]67[.]220[.]21
- 172[.]67[.]186[.]21
- 199[.]59[.]242[.]153
- 104[.]18[.]42[.]18
- 91[.]195[.]240[.]117
- 111[.]90[.]159[.]60
- 111[.]90[.]158[.]115
- 185[.]35[.]137[.]50
- 192[.]187[.]111[.]219
- 192[.]187[.]111[.]222
- 81[.]17[.]18[.]197
- 185[.]11[.]145[.]111
- 192[.]187[.]111[.]220
- 185[.]61[.]137[.]47
- 192[.]187[.]111[.]221
- 185[.]107[.]56[.]200
- 185[.]107[.]56[.]199
- 206[.]221[.]176[.]184
- 104[.]27[.]183[.]84
- 185[.]107[.]56[.]198
- 104[.]27[.]182[.]84
- 45[.]33[.]2[.]79
- 104[.]28[.]30[.]74
- 37[.]48[.]65[.]149
- 104[.]28[.]31[.]74
- 198[.]58[.]118[.]167
- 172[.]67[.]132[.]84
- 96[.]126[.]123[.]244
- 172[.]67[.]132[.]168
- 45[.]56[.]79[.]23
- 104[.]28[.]22[.]69
- 45[.]33[.]23[.]183
- 104[.]28[.]23[.]69
- 70[.]32[.]1[.]32
- 104[.]18[.]39[.]6
- 45[.]79[.]19[.]196
- 172[.]67[.]222[.]148
- 104[.]21[.]38[.]117
- 104[.]18[.]38[.]6
- 5[.]23[.]54[.]176
- 172[.]67[.]146[.]63
- 77[.]244[.]219[.]37
- 103[.]255[.]237[.]10
- 104[.]21[.]81[.]198
- 52[.]0[.]217[.]44
- 111[.]90[.]141[.]122
- 185[.]11[.]145[.]5
- 103[.]155[.]93[.]116
- 103[.]155[.]93[.]184
- 104[.]27[.]158[.]198
- 104[.]27[.]159[.]198
- 192[.]161[.]187[.]200
- 172[.]67[.]173[.]84
- 209[.]141[.]38[.]71
- 107[.]161[.]23[.]204
- 188[.]225[.]9[.]25
- 104[.]21[.]80[.]22
- 199[.]33[.]112[.]226
- 81[.]90[.]180[.]214
- 103[.]224[.]212[.]220
- 170[.]178[.]168[.]203
- 35[.]203[.]17[.]246
- 185[.]107[.]56[.]52
- 162[.]210[.]195[.]123
- 192[.]157[.]56[.]142
- 207[.]244[.]67[.]139
- 207[.]244[.]67[.]138
- 162[.]210[.]196[.]166
- 162[.]210[.]195[.]122
- 162[.]210[.]199[.]65
- 192[.]157[.]56[.]141
- 162[.]210[.]199[.]87
- 185[.]99[.]133[.]188
- 46[.]249[.]59[.]121
- 104[.]24[.]101[.]187
- 47[.]254[.]216[.]171
- 104[.]24[.]100[.]187
- 104[.]28[.]27[.]206
- 172[.]67[.]152[.]209
- 190[.]115[.]18[.]179
- 45[.]9[.]148[.]209
- 1[.]1[.]1[.]1
- 190[.]115[.]18[.]186
- 31[.]202[.]2[.]61
- 31[.]220[.]2[.]61
- 91[.]241[.]19[.]61
- 185[.]104[.]114[.]189
- 94[.]242[.]224[.]214
- 185[.]99[.]133[.]68
- 185[.]162[.]11[.]77
- 185[.]77[.]128[.]109
- 185[.]20[.]185[.]228
- 188[.]209[.]49[.]192
- 104[.]247[.]81[.]13
- 188[.]209[.]49[.]71
- 185[.]161[.]209[.]58
- 45[.]9[.]150[.]24
- 149[.]3[.]170[.]39
- 104[.]18[.]54[.]149
- 104[.]18[.]55[.]149
- 185[.]61[.]137[.]58
- 185[.]255[.]179[.]78
- 81[.]177[.]23[.]102
- 185[.]61[.]137[.]52
- 185[.]219[.]42[.]117
- 185[.]135[.]83[.]120
- 78[.]24[.]223[.]204
- 185[.]244[.]43[.]42
- 185[.]115[.]140[.]154
- 185[.]20[.]187[.]160
- 3[.]13[.]31[.]214
- 5[.]8[.]76[.]180
- 88[.]212[.]253[.]133
- 208[.]69[.]117[.]124
- 151[.]248[.]123[.]92
- 185[.]180[.]198[.]111
- 5[.]188[.]9[.]54
- 194[.]67[.]104[.]103
- 185[.]11[.]145[.]249
- 104[.]27[.]128[.]248
- 185[.]62[.]190[.]13
- 185[.]61[.]137[.]99
- 104[.]27[.]129[.]248
- 172[.]67[.]159[.]6
- 190[.]115[.]21[.]170
- 104[.]21[.]58[.]107
- 185[.]61[.]137[.]49
- 91[.]220[.]101[.]41
- 107[.]150[.]98[.]48
- 104[.]28[.]22[.]40
- 179[.]43[.]176[.]223
- 172[.]67[.]130[.]129
- 104[.]28[.]23[.]40
- 104[.]21[.]3[.]85
- 47[.]74[.]0[.]181
- 47[.]74[.]8[.]123
- 64[.]32[.]8[.]69
- 46[.]166[.]182[.]113
- 64[.]32[.]8[.]68
- 185[.]107[.]56[.]59
- 63[.]143[.]32[.]85
- 64[.]32[.]8[.]67
- 185[.]107[.]56[.]58
- 185[.]107[.]56[.]57
- 63[.]143[.]32[.]89
- 64[.]32[.]8[.]70
- 185[.]107[.]56[.]60
- 63[.]143[.]32[.]91
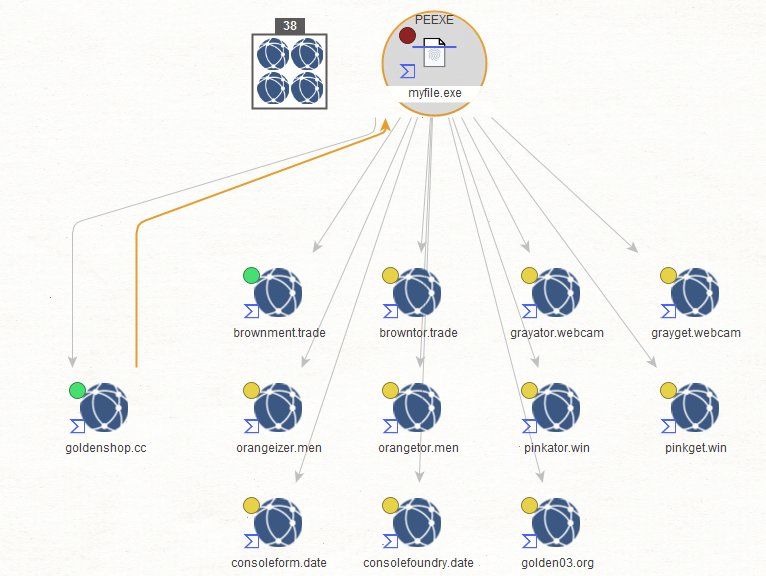
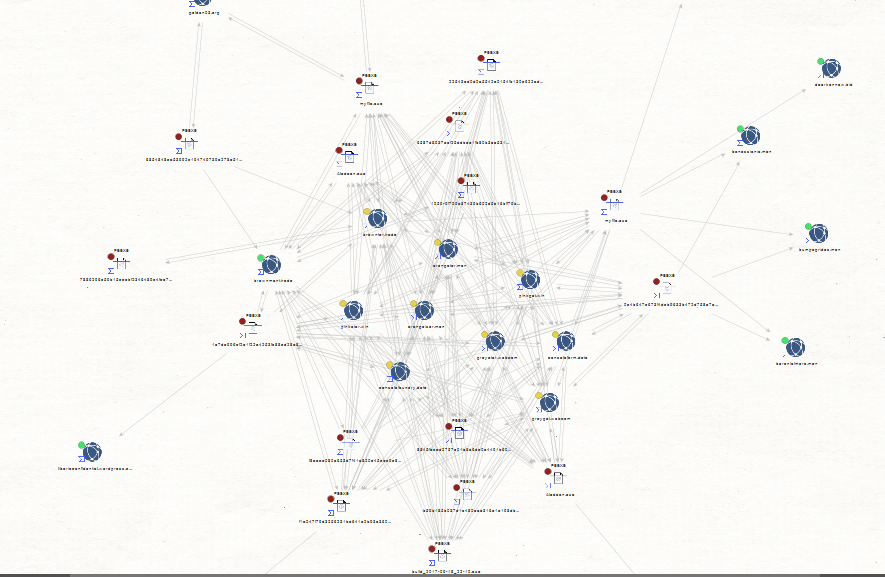
Sample C&C Phone back domains known to have phoned back to the same infrastructure:
- kingven[.]cc
- goldenshop[.]cc
- beranielmarc[.]men
- mrwhite[.]biz
- bumpogrides[.]men
- greendumps24[.]biz
- russianmarket[.]gs
- banessionia[.]men
- luckytrack[.]cc
- shadowcarders[.]com
- pabloescobar[.]biz
- stardumps24[.]com
- russianmarket[.]zone
- topcc[.]store
- smd1[.]la
- briansclub[.]at
- tiesto[.]ec
- brocard1[.]net
- bestdumps[.]biz
- www[.]longbucks[.]com
- www[.]forexpeacearmy[.]com
- fullzstore[.]su
- goodshopbiz[.]net
- fullzshop[.]su
- wt1[.]la
- liberiaconfidential[.]wordpress[.]com
- wt1shop[.]org
- yohohobay[.]cc
- swipe[.]bz
- c2bit[.]pw
- briansclub[.]cm
- cardhouse[.]cc
- buybestbiz[.]net
- deluxedumps[.]com
- carderbay[.]com
- ebin[.]cc
- ddumps24[.]com
- fe-shop[.]link
- diamondumps[.]biz
- freshstuff24[.]net
- the-airmoney[.]ru
- entershop[.]st
- bestdump[.]org
- flyded[.]gs
- vendta[.]cc
- worldcvv[.]me
- grayget[.]webcam
- orangeizer[.]men
- coachlointe[.]men
- browntor[.]trade
- grayator[.]webcam
- brownment[.]trade
- consolefoundry[.]date
- golden03[.]org
- pinkget[.]win
- consoleform[.]date
- orangetor[.]men
- doerkennaw[.]bid
- pinkator[.]win
Related malicious phone back C&C domains known to have been part of the botnet’s infrastructure:
- rb-authorize[.]cz
- linkworkers[.]xyz
- amnsns[.]com
- powerprivat[.]ru
- c[.]mogrodeerc[.]org
- swedlv-private[.]site
- authorize-online[.]rest
- globalblockchain-wallet24[.]com
- vot552[.]com
- unicr-client[.]online
- client-finance[.]site
- dsntu[.]top
- offce221[.]com
- client-ucbb[.]online
- gernnnolr[.]ru
- ftp[.]probeerpil[.]ru
- elienne[.]net
- bulbaknoline[.]online
- vintrsi[.]com
- klii[.]org
- usaa-onlineservice[.]com
- www[.]regeneration-data[.]at
- gernnnol[.]ru
- dandylinos[.]com
- zendenotech[.]com
- overplayninsx[.]xyz
- greenfrunze[.]com
- 7zipd[.]com
- m[.]omerta[.]cc
- video[.]thefreshstuffs[.]at
- heygamersnort[.]at
- securerbczechbank[.]online
- tem7ex1ktgjvbmibqk4vzu86[.]file[.]truckbennels[.]com
- bankczechrbtech[.]online
- far[.]spargroarr[.]org
- alertrb[.]online
- u6eqx54quk004c1feumrvnqw[.]file[.]truckbennels[.]com
- onlinerbgass[.]site
- authorize-rb[.]casa
- client-rb[.]casa
- b[.]roprolecv[.]org
- a[.]roprolecv[.]org
- 6433f[.]update[.]weeklywordsofwisdom[.]com
- pexizzf1762zihg2vkida812[.]file[.]truckbennels[.]com
- hex001[.]info
- 7a10[.]download[.]thesongwritercollection[.]com
- 3v6bz7g2bncvrinwmaawz2t4[.]file[.]truckbennels[.]com
- ntrcopz[.]com
- securemrc[.]ru
- securerbczech[.]online
- rbanksecure[.]online
- file[.]truckbennels[.]com
- stoutorder[.]xyz
- bulbankonilne[.]email
- online-rb[.]email
- ritus14[.]synology[.]me
- client-rb[.]email
- raiffelsenrb-online[.]online
- verify-acc1required[.]com
- authorize-rb[.]email
- authorize-client[.]email
- ww2[.]ukmoneyaq[.]cn
- de[.]heygamersnort[.]at
- mobi[.]verify-acc1required[.]com
- babynibble[.]com
- pi[.]fonderfonds[.]at
- gameclockersd[.]com
- c[.]roprolecv[.]org
- d[.]roprolecv[.]org
- bankraifcz[.]online
- onlinerb[.]pro
- www[.]datdepot[.]net
- bulbankonlne[.]email
- www[.]rxmedworld[.]com
- datdepot[.]net
- tinnys[.]monster
- oversun[.]monster
- netvxi[.]com
- rxmedworld[.]com
- oversun[.]net
- dingobossin[.]com
- jamb2[.]monster
- uqtbpamsitrvstqacjpzre[.]com
- mfdyzx[.]com
- www[.]kitsapharborfestival[.]com
- knejjwugtxwgrpf[.]su
- safegross[.]com
- handous[.]net
- cathits[.]net
- cvvunion[.]at
- usaa-membersupport[.]com
- bulbank[.]email
- fonderfonds[.]at
- navyderal-urgent[.]com
- firoprinterstrog[.]com
- quickbooks-intuits[.]com
- medastr[.]com
- www[.]digispiel[.]co
- kreewalk[.]com
- schwabsoffice[.]com
- chaseonlinebusinessc[.]com
- m[.]zonaykan[.]com
- chaseonlinedebit1[.]com
- waiireme[.]com
- www[.]thefreshstuffs[.]se
- zonaykan[.]com
- kupitorta[.]net
- thefreshstuffs[.]se
- cmarcite[.]net
- accountants[.]msk[.]ru
- vairina[.]top
- marcoplfind[.]at
- www[.]netflix-support[.]top
- inferno-girls[.]at
- armyoffers[.]com
- netflix-support[.]top
- tequlinersin[.]com
- nykidsfw[.]com
- njwhuclqpvvwhwg[.]ru
- cipluks[.]com
- al-commandoz[.]com
- camdanoda[.]com
- ns4[.]cloudflag[.]ru
- ns3[.]cloudflag[.]ru
- zoa5533[.]xyz
- fuck00001[.]com
- mail[.]thefreshstuffs[.]at
- teslalove-one[.]org
- onlinrb[.]cz
- bananinze[.]com
- myservicetoonic[.]com
- gensoterman[.]com
- perseus007[.]xyz
- gutalinsons[.]com
- lambos1[.]xyz
- schwabs-message[.]com
- b[.]hotspotllc[.]com
- ns3[.]bizzznez[.]org
- secure-membershipcard[.]com
- d[.]bizzznez[.]org
- chaseonline-messages[.]com
- orderlynet[.]net
- a[.]bizzznez[.]org
- thefreshstuffs[.]org
- c[.]bizzznez[.]org
- b[.]bizzznez[.]org
- thefreshstuff[.]at
- c[.]hotspotllc[.]net
- www[.]thefreshstuff[.]at
- www[.]thefreshstuffs[.]org
- a[.]hotspotllc[.]net
- b[.]hotspotllc[.]net
- cloud-start[.]at
- usaa-memberservices[.]com
- d[.]hotspotllc[.]net
- chaseonline-supports[.]com
- cdnjsapis[.]com
- waruse[.]com
- ww[.]usaa-onlineservice[.]com
- chasecardsolutions1[.]com
- www[.]bascif[.]com
- admin[.]admin[.]admin[.]admin[.]admin[.]admin[.]admin[.]admin[.]admin[.]admin[.]admin[.]admin[.]www[.]klll[.]at
- chasecardsolutionsw[.]com
- bascif[.]com
- www[.]njwhuclqpvvwhwg[.]ru
- jbswin[.]net
- admin[.]admin[.]admin[.]admin[.]admin[.]www[.]klll[.]at
- somfyexpert[.]ro
- ns1[.]bizzznez[.]org
- intrade-support[.]at
- ns4[.]bizzznez[.]org
- anumal-planet[.]at
- to4karu[.]ru
- hrapplications[.]org
- primankanamanky[.]ru
- cartoons-online[.]at
- lovely-mike[.]xyz
- mrcsecure[.]ru
- taslks[.]at
- dossecure[.]ru
- zxciuniqhweizsds[.]com
- goose-mongoose[.]at
- living-start[.]at
- winserver-cdn[.]at
- limpopo[.]at
- estate-advice[.]at
- roiboypo[.]ru
- blackpass[.]info
- vgerkisv[.]com
- roiboypoka[.]ru
- woatdert[.]com
- rbonline[.]email
- fantaniz[.]ru
- litmanses[.]at
- snezhkaie[.]ru
- regutalor-stat[.]at
- vuterfaste[.]ru
- promokonyara[.]ru
- usaacustomerservice[.]com
- tahhir[.]at
- mnogonimalo[.]ru
- esventura[.]com
- usaa-membershipst[.]com
- 1chaseonlineserices[.]com
- blackl1vesmatter[.]org
- fuck022551[.]ru
- goodwoodmood[.]at
- x-100new[.]com
- raiffeisenalert[.]online
- teslalove-two[.]org
- bigpresense[.]top
- schwabs-urgentalert[.]com
- www[.]schwabs-urgentalert[.]com
- thefreshstuffs[.]mu
- bitexplorer[.]at
- validcc[.]mn
- secureccvip[.]ru
- roiboypoleno[.]ru
- rbgassonline[.]work
- onlineraifgass[.]host
- onlineraiffcz[.]vip
- rbgassonline[.]cyou
- online-rbcz[.]icu
- onlinerbgassspec[.]pro
- everydayparty[.]xyz
- vip-statistic[.]at
- ns3[.]klii[.]org
- myhomesitter[.]fun
- mashallah[.]at
- trueglovers[.]com
- luxerooprar[.]com
- cullinan[.]at
- furhatsth[.]net
- wellsfargosz[.]com
- www[.]mfdyzx[.]com
- intraders-support[.]at
- sweetlights[.]at
- shoshanna[.]at
- ns4[.]klii[.]org
- ns2[.]klii[.]org
- ns1[.]klii[.]org
We’ll continue monitoring this botnet’s fast-flux and C&C hosting infrastructure and will issue updates as soon as new developments occur.
Read other articles



































